Scan Dependency Vulnerabilities
Nowadays, real world products often include lots of open source components. It's crucial to periodically scan these components to detect any security vulnerabilities and update them promptly to prevent potential attacks.
In this tutorial, we demonstrate how to set up CI/CD jobs to detect security vulnerabilities in an example project. This project relies on some npm modules which is recorded in yarn.lock, and some python packages which is recorded in requirements.txt. The CI/CD job scan vulnerabilities is created to detect security vulnerabilities of these components:
- It comprises of two steps. Step checkout clones the project into job workspace, and step scan scans the job workspace recursively to find vulnerabilities of components defined in various lock files. The scan step will fail the build if it finds vulnerabilities with HIGH or CRITICAL severity via Fail Threshold property
- In Params & Triggers section of the job, two job triggers are defined. The first runs the job whenever yarn.lock or requirements.txt is changed in any branch, and the second runs the job periodically at 1:00 AM every day for all branches in case new vulnerabilities are disclose
- In More Settings section of the job, a post build action is defined to send notification to relevant person if current build is failed while previous build was successful. This avoids sending notification repeatedly for continuous build failures.
After build finishes, found vulnerabilities will be displayed in a tab specified via property Report Name in scan step like below:
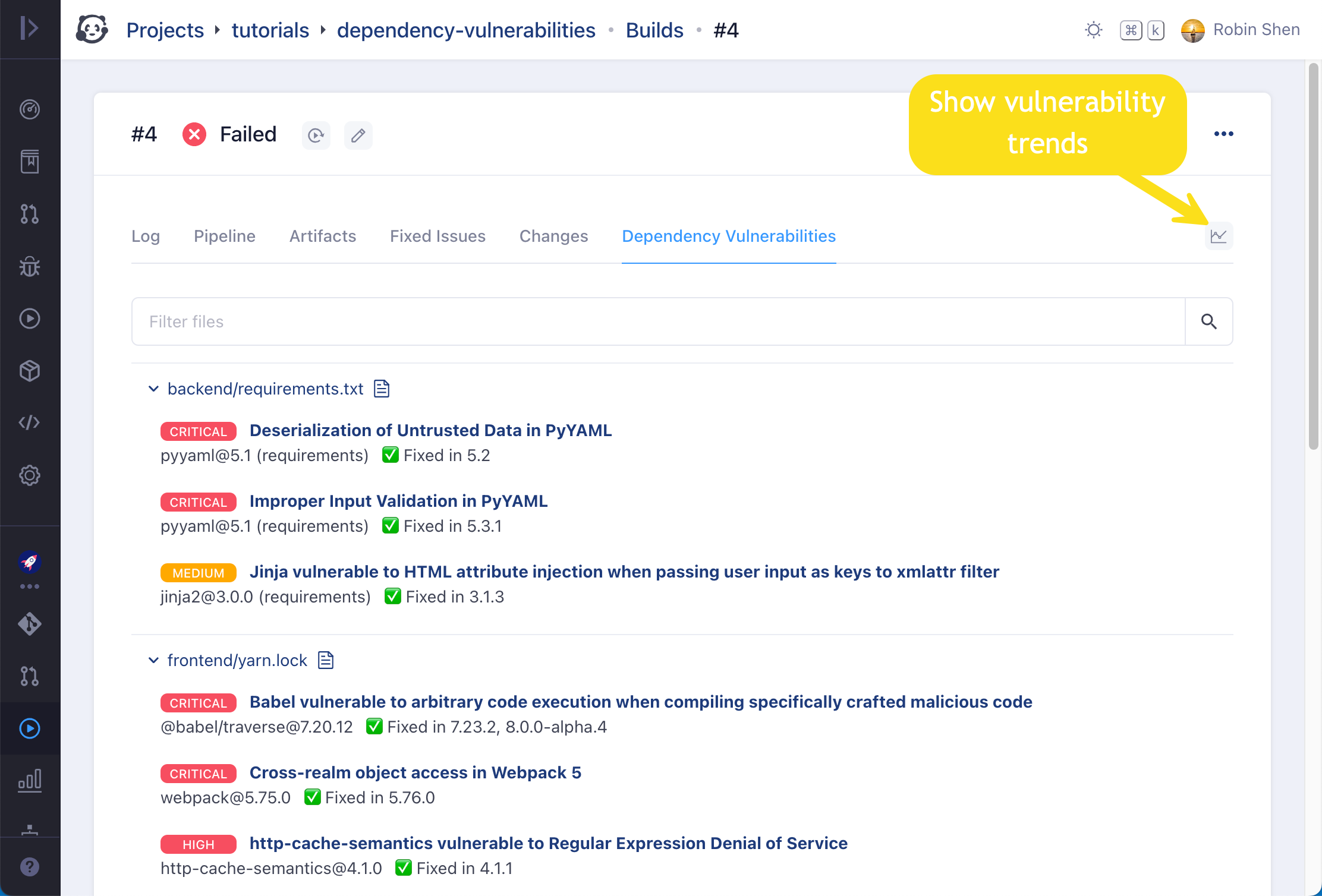
Since the vulnerability check is designed as an ordinary CI/CD job, it can leverage existing CI/CD facilities to do a lot of useful things, for instance, to create issue when job fails, to make it a prerequisite of other jobs via job dependency, to require the job successful when merge code to protected branches, or to configure appropriate role so that vulnerability report is only accessible to certain users.