Insecure Docker Registry
Your CI/CD build might need to interact with insecure docker registry running with http protocol or self-signed certificate. This tutorial explains how to achieve this with docker related executors.
Configure Docker Daemon
Edit /etc/docker/daemon.json on all machines docker executor might be running to add insecure registries like below:
{
"insecure-registries" : [ "<registry host>:<registry port>" ]
}
Then restart docker daemon by running sudo systemctl restart docker
Configure Docker Builder
Firstable we need to check which builder is being used in more settings of the executor executing your job:
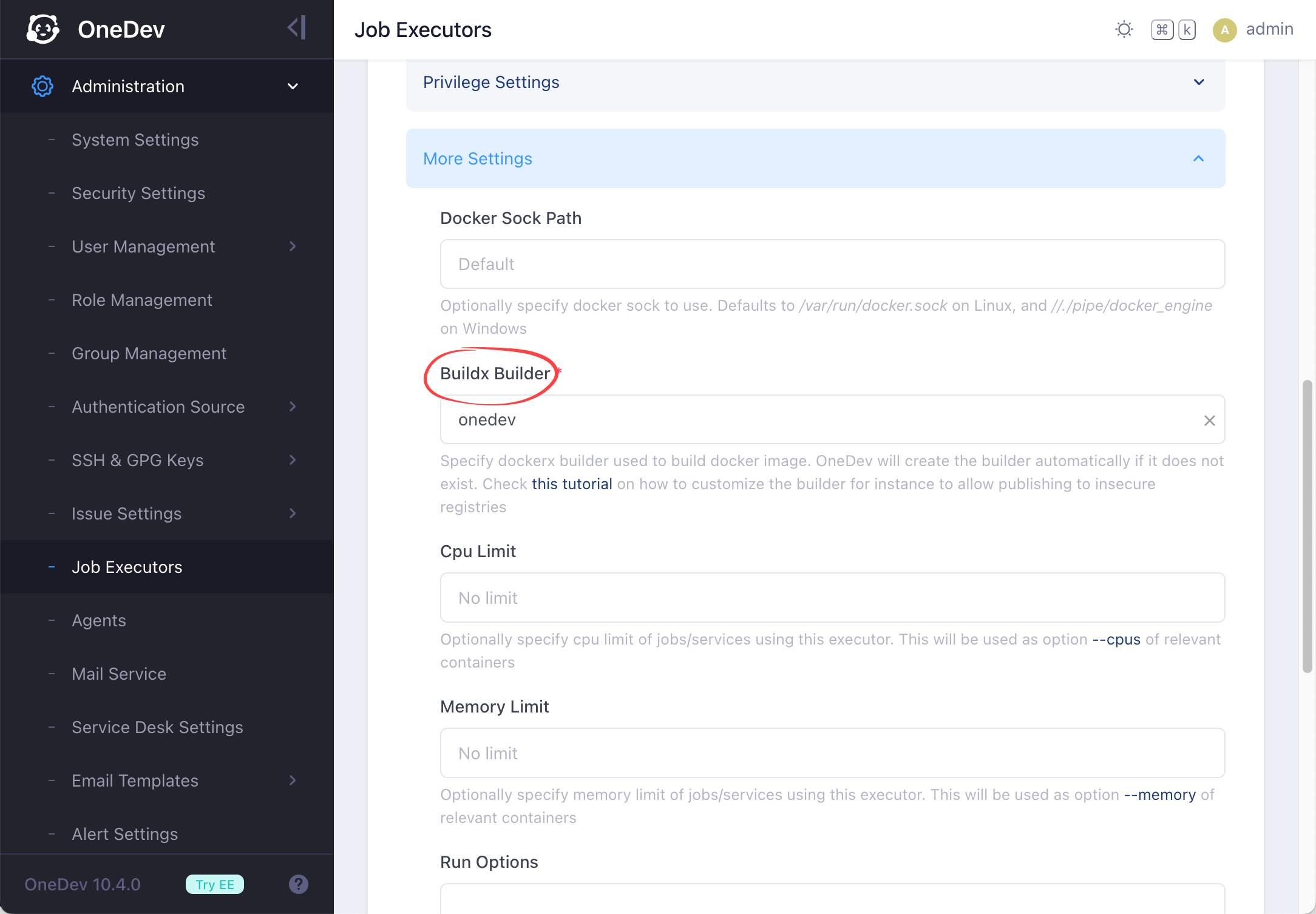
By default the builder onedev is used for all executors, including the auto-discovered one
On all machines the executor might be running, login as the OS user running OneDev process if OneDev server or agent runs in bare metal mode, or any user with docker run permission if it runs inside docker container. Then do the following:
-
Run below command to delete the builder:
docker buildx rm <builder name> -
Run
docker ps -a|grep buildx_buildkit_<builder name>0to list associated builder container. Delete the container if it exists -
Create a file say /etc/buildkit/buildkitd.toml containing below content:
[registry."<registry host>:<registry port>"]
http = true -
Create the builder using above file as config file:
docker buildx create --name <builder name> --config /etc/buildkit/buildkitd.toml -
If OneDev runs inside docker container, you also need to mount the buildx config into the container via below option so that the builder can be accessed inside container, for instance:
docker run --name onedev -d --restart always -v <host docker sock>:/var/run/docker.sock -v <data dir>:/opt/onedev -v <user home>/.docker/buildx:/root/.docker/buildx -p 6610:6610 -p 6611:6611 1dev/server