LetsEncrypt Setup with Kubernetes
This tutorial explains how to deploy OneDev into a Kubernetes cluster to get a full-blown CI/CD farm, and protect it with LetsEncrypt.
We will demonstrate with Google Kubernetes Engine, which is the most convenient to set up and maintain according to my experience.
-
Create a standard GKE cluster with all default options
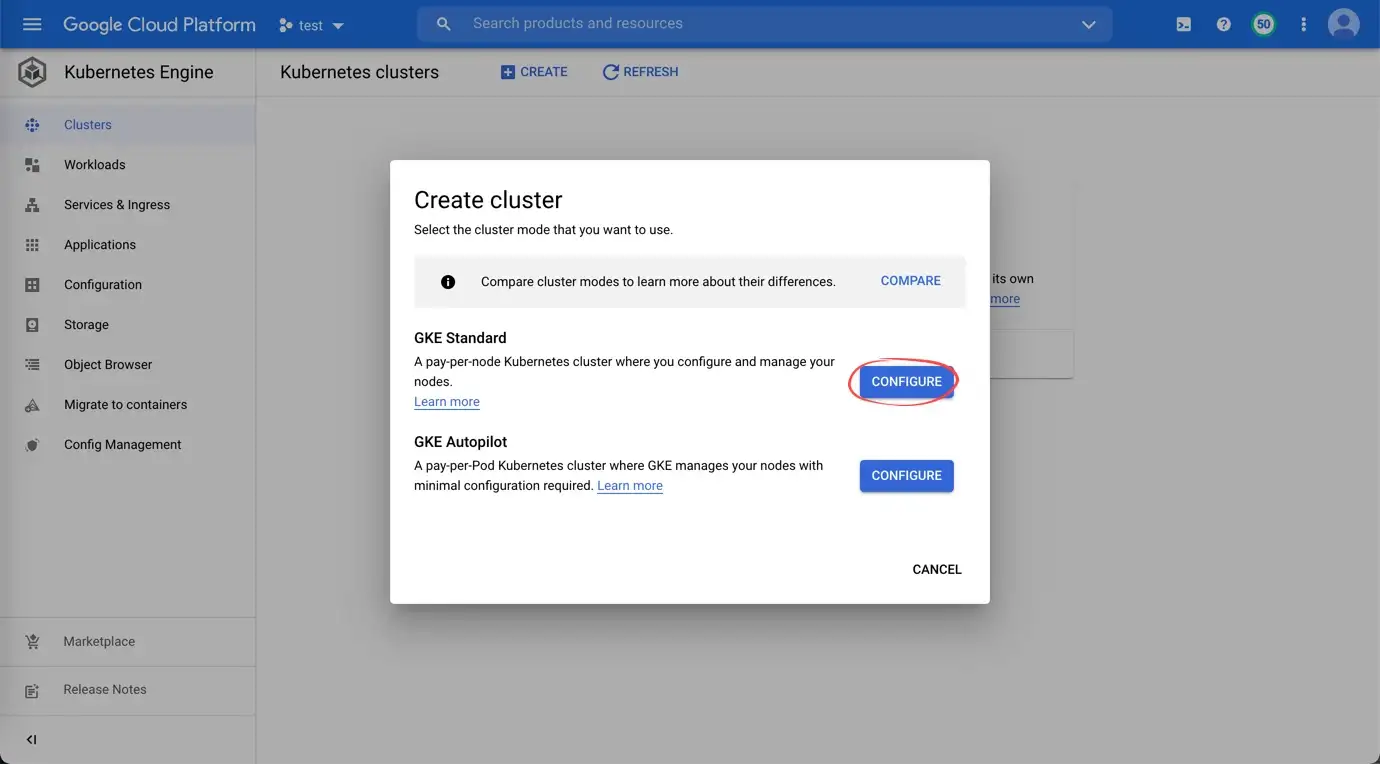
-
After cluster is created, configure kubectl to connect to the cluster
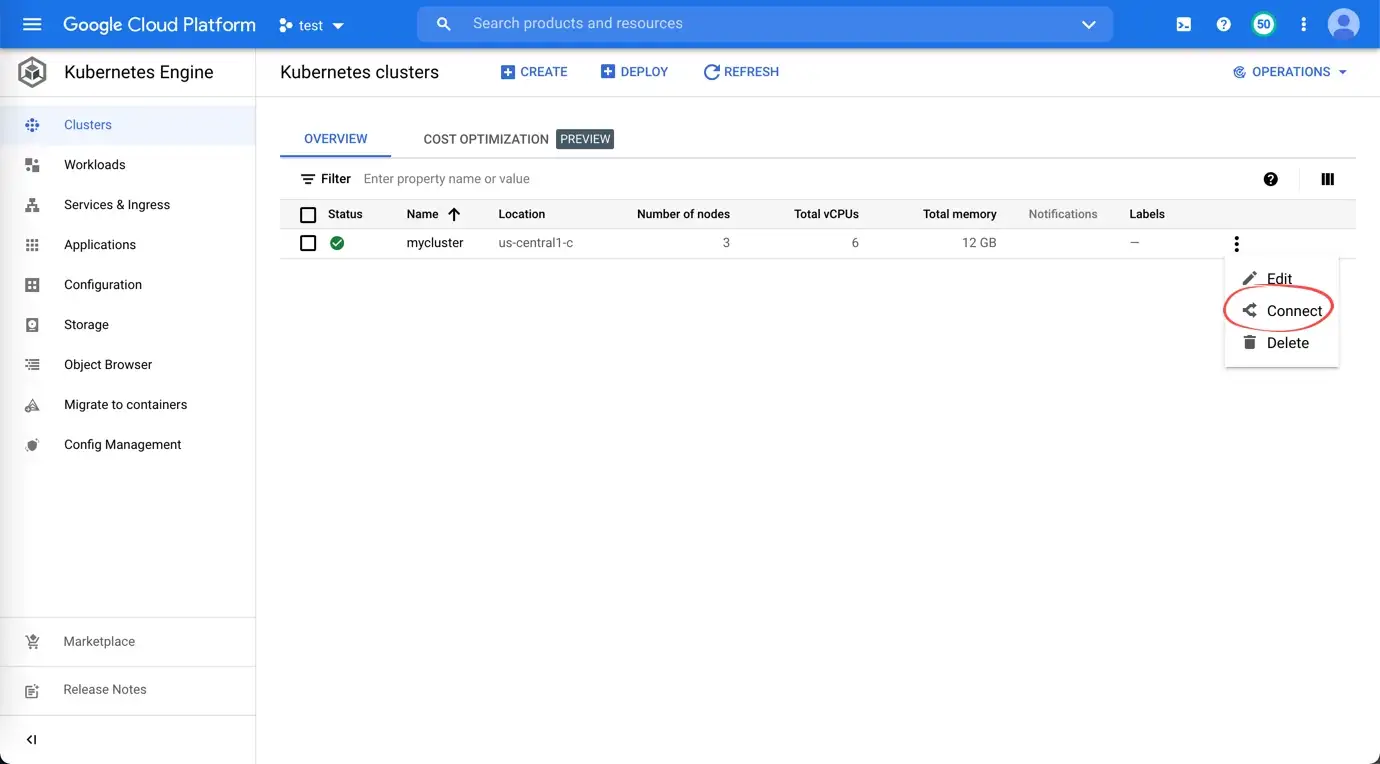

-
Make sure helm is installed, run below commands to install ingress Nginx controller and cert manager:
$ helm install ingress-nginx ingress-nginx --repo https://kubernetes.github.io/ingress-nginx --namespace ingress-nginx --create-namespace
$ kubectl apply -f https://github.com/jetstack/cert-manager/releases/download/v1.6.0/cert-manager.yaml -
Run below command to get external ip address of nginx controller:
$ kubectl get service ingress-nginx-controller -n ingress-nginx -
Configure your dns provider to add a
Arecord to associate OneDev DNS name with external ip address above. Wait for some time for the DNS entry to spread out (you may ping the DNS name to see if it returns the correct ip address to make sure) -
Now deploy OneDev into the cluster with below command (replacing
<OneDev DNS name>with above DNS name, and<your email address>with an email address using to receive LetsEncrypt certificate notifications):$ helm install onedev onedev --repo https://code.onedev.io/onedev/~helm --namespace onedev --create-namespace --set ingress.enabled=true --set ingress.className=nginx --set ingress.host=<OneDev DNS name> --set ingress.tls.enabled=true --set ingress.tls.acme.enabled=true --set ingress.tls.acme.email=<your email address> --set ingress.tls.acme.production=trueFor a complete list of configurable values of OneDev chart, please check the values.yaml file
-
Wait a while for OneDev to get deployed. If things work fine, you should be able to visit OneDev at
https://<OneDev DNS name>follow In case it does not work, follow this guide to trouble shoot certificateonedev-tlsin namespaceonedev -
If you also want to enable SSH access to OneDev repositories, run below command to configure tcp port of the Nginx controller
helm upgrade ingress-nginx ingress-nginx --repo https://kubernetes.github.io/ingress-nginx -n ingress-nginx --set tcp.22=onedev/onedev:ssh --reuse-valuesThen update
SSH Root URLat OneDev side (via menu Administration / System Setting) asssh://<OneDev DNS name>
Thanks for reading!